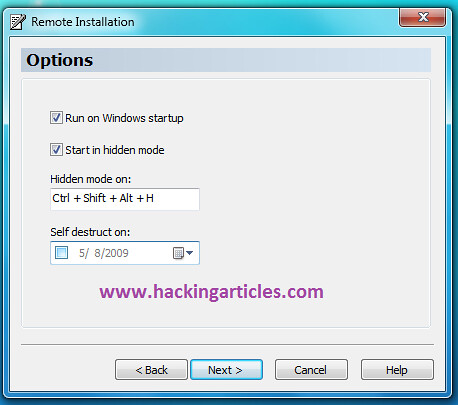
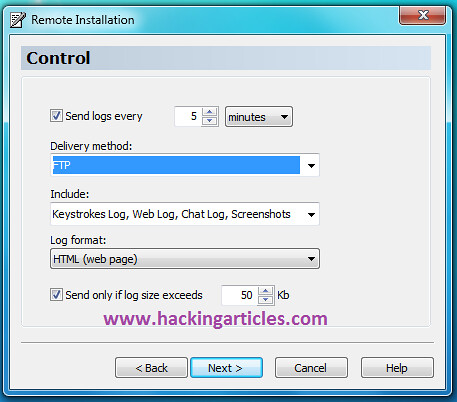
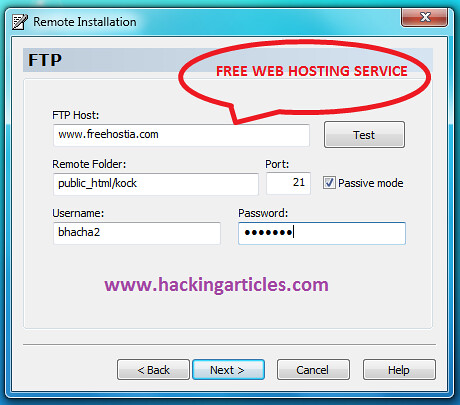
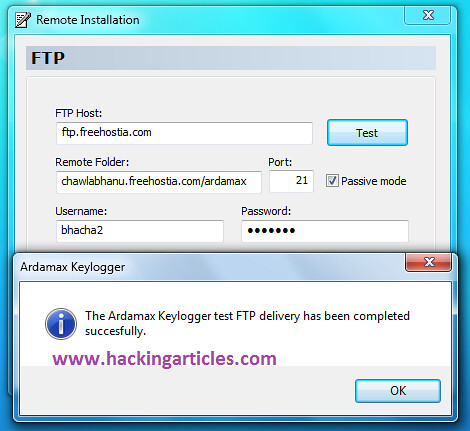
Friends, many of you download files from some file-sharing sites like rapidshare, hotfile, megaupload etc.
We all know that they provide download after some time waiting and even they also give us low speed download without resume if we choose free user download.
You can also download from this file sharing sites as premium user to download files fast without waiting but for that we have to pay some dollars to them so I will today introduce you to a one awesome website which provides us to download from this file sharing websites as premium user for FREE !!
And This website www.fileflyer.com/filefetch
Just go to above URL and paste your download link of file sharing websitesAfter that Enter your email id
And on check on box of Terms And Condition
Now finally click on fetch
And voila your file has been uploaded to fileflyer server.
NOW They will send you a download link in Ur email inbox.
click on that link and press on download button and your download will start without waiting with resume support from high speed servers.
IF U LIKE THIS POST THEN SHARE IT ON SOCIAL NETWORKING WEBSITES AND DON'T FORGET TO DO COMMENTS ON THIS POST.
We all know that they provide download after some time waiting and even they also give us low speed download without resume if we choose free user download.
You can also download from this file sharing sites as premium user to download files fast without waiting but for that we have to pay some dollars to them so I will today introduce you to a one awesome website which provides us to download from this file sharing websites as premium user for FREE !!
And This website www.fileflyer.com/filefetch
Just go to above URL and paste your download link of file sharing websitesAfter that Enter your email id
And on check on box of Terms And Condition
Now finally click on fetch
And voila your file has been uploaded to fileflyer server.
NOW They will send you a download link in Ur email inbox.
click on that link and press on download button and your download will start without waiting with resume support from high speed servers.
IF U LIKE THIS POST THEN SHARE IT ON SOCIAL NETWORKING WEBSITES AND DON'T FORGET TO DO COMMENTS ON THIS POST.


 Tweaked USB that steals every password including licenses.
Tweaked USB that steals every password including licenses.